In the rapidly evolving world of software development, dependency security stands as a critical line of defense against cyber threats, particularly in environments accelerated by AI-generated code, where the speed and complexity of development can obscure potential vulnerabilities. This blog delves deeper into the technical aspects of Software Composition Analysis (SCA) and dependency scanning, explaining why these tools are indispensable for modern cybersecurity strategies.
Deep Dive into Software Composition Analysis (SCA)
Software Composition Analysis (SCA) is an advanced toolset designed for identifying and managing the open-source components and dependencies within software projects. It serves as a cornerstone for DevSecOps by integrating security measures early in the software development lifecycle (SDLC).
How SCA Tools Operate
SCA tools function by scanning software repositories to create a detailed Software Bill of Materials (SBOM). This SBOM lists every component, detailing versions, licensing information, and security vulnerabilities. The process taps into extensive databases, such as the National Vulnerability Database (NVD) and proprietary repositories like Synopsys’s Black Duck® KnowledgeBase, to assess and identify potential risks.
The Technical Benefits of SCA
The primary advantage of SCA tools lies in their ability to automate the detection and management of vulnerabilities and licensing issues. This automation supports high development speeds without compromising on security or compliance, crucial in maintaining the integrity of complex software projects.
Integration and Continuous Improvement
With the increasing reliance on open-source software, the complexity of applications has grown exponentially, making manual tracking of vulnerabilities nearly impossible.
Modern SCA solutions, seamlessly integrate into existing CI/CD pipelines, enabling continuous analysis and feedback. This integration is pivotal for the "shift left" security approach, allowing teams to address vulnerabilities as soon as they are introduced into the codebase.

The Critical Role of Dependency Scanning in Cybersecurity
Dependency scanning is a specialized aspect of SCA that focuses on the vulnerabilities within the dependencies of a software project. It is your first line of defense against supply chain attacks, which can exploit third-party vulnerabilities to compromise entire systems.
How Dependency Scanning Works
Dependency scanners analyze both direct dependencies (libraries directly included by developers) and transitive dependencies (libraries included by those direct dependencies). They track these through package managers and manifest files, employing recursive techniques to unearth vulnerabilities that might otherwise remain hidden within dependency chains.
Benefits of Effective Dependency Management
Proactive dependency management through scanning allows developers to address vulnerabilities before they become exploitable. This not only enhances security but also maintains the integrity of the development process, ensuring that applications are both secure and performant upon deployment.
Integrating SCA and Dependency Scanning in Development Workflows
At Vidoc Security Lab, we embed SCA and dependency scanning directly into development workflows via GitHub Actions. This strategy not only enhances security but also maintains the agility needed in AI-driven development environments.
Automation Benefits
By automating the scanning and analysis processes, our tool provide continuous insights into security posture and compliance status, crucial for ongoing threat assessment and mitigation.
Prioritization and Patch Management
Our advanced VIDOC tool does more than just detect vulnerabilities; it also prioritizes vulnerabilities based on the risk they pose and provides actionable remediation guidance which may include patching or updating components. This approach ensures that the most critical vulnerabilities are addressed promptly, minimizing potential exposure, and streamlining the resolution process by reducing downtime.
Conclusion: Why Dependency Security Should Be a Priority
Dependency security, powered by SCA and dependency scanning, is foundational to securing software systems against the backdrop of increasing dependency on open-source components and rapid development cycles. It also provides the necessary oversight to manage the risks associated with third-party software components, ensuring that applications are both secure and compliant.
At Vidoc Security Lab, our cutting-edge technology is designed to address the modern challenges of AI-generated code, making dependency security more crucial than ever. Our AI Security Engineer tool, equipped with capabilities like Software Composition Analysis (SCA), Dynamic and Static Application Security Testing (DAST and SAST), and secret detection, is integrated directly into your development pipeline via GitHub Actions. Unlike traditional tools, our AI not only identifies security issues but also understands code context to accurately validate potential false positives and provides actionable code snippets for quick remediation.
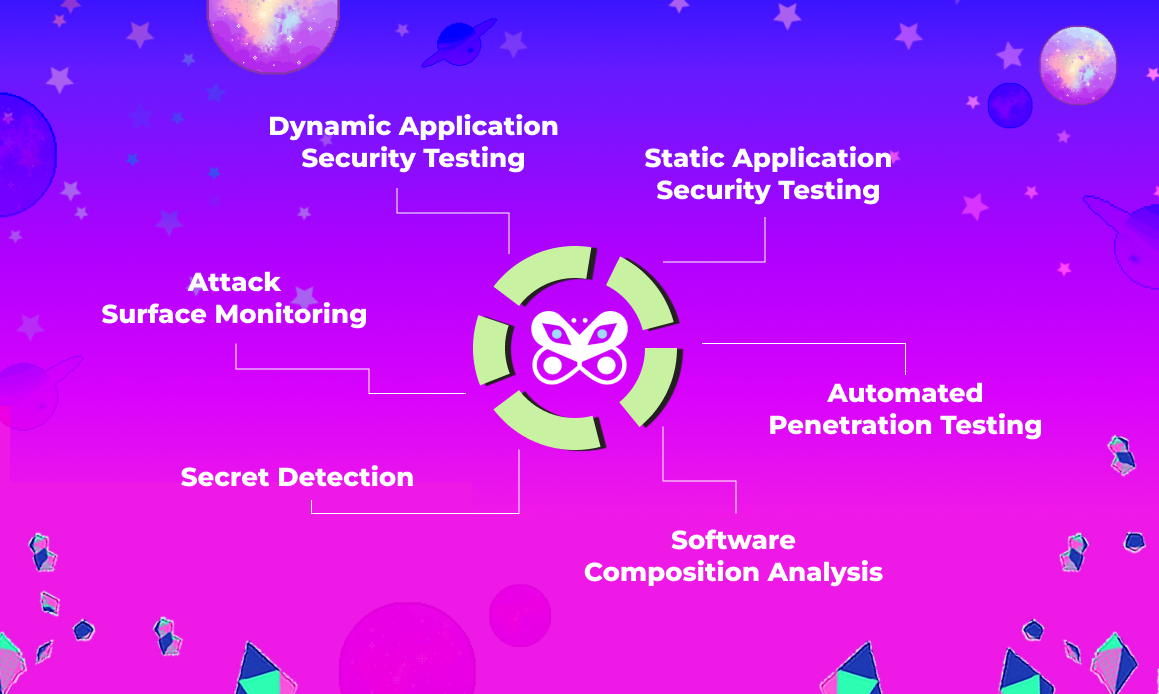
By choosing Vidoc Security Lab, you are not just applying a security tool; you are integrating a proactive, intelligent security engineer into your team. This approach ensures that your software remains robust, secure, and compliant amidst the rapidly evolving landscape of cyber threats. Try our tool today to protect your software with the most advanced SCA technology available.
_________________________________________________________
Check our other social media platforms to stay connected:
Website | www.vidocsecurity.com
Linkedin | www.linkedin.com/company/vidoc-security-lab
X (formerly Twitter) | twitter.com/vidocsecurity
YouTube | www.youtube.com/@vidocsecuritylab
Facebook | www.facebook.com/vidocsec
Instagram | www.instagram.com/vidocsecurity
